Meetup Sécurité - AWS - Recap Reinforce 2019
- 2. équipe Meetup Julien Bichon Community ambassador @jubichon Talk 1 Back From Re:inforce Stephan Hadinger & Christine Grassi Talk 2 Les “Boundary Policy” Jérémie Rodon 🍕🍕🍕🍻🍻🍻
- 3. Slack AWS User Group Échangez et posez vos questions aux experts AWS. https://bit.ly/awsfrmeetup
- 4. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Re:inforce Recap 2019 Stephan Hadinger – Head of Technology, AWS France Christine Grassi – Security practice lead, D2SI
- 5. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Agenda 1. Introduction au re:Inforce 2. Keynote : messages clés 3. Focus sur quelques annonces 4. Conclusion
- 6. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Agenda 1. Introduction au re:Inforce 2. Keynote : messages clés 3. Focus sur quelques annonces 4. Conclusion
- 7. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
- 8. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved.
- 9. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Agenda 1. Introduction au re:Inforce 2. Keynote : messages clés 3. Focus sur quelques annonces 4. Conclusion
- 10. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Key notes : messages clés (1/7) Behavior Features Learning
- 11. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Key notes : messages clés (2/7) Behavior Features Learning “Teach your dev. engineers where they've made errors ... and help them prevent those errors in the future, since no tool will ever be perfect.” “It is not just the job of the security professionals who are in this room today, but every developer who's out there,” “Open minded” & “Eagerness to learn” (Liberty) « We’re not signing people up for credit cards »
- 12. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Faire de la sécurité un avantage concurrentiel (Capital One) Automatisation (contrôles & remediation) Flexibilité (REX) DevSecOps : “the way ops happens” “One of the most important things we can do as a security industry is build in the right behavior profiles for our staff. (...) That means building behavior in both the security engineering teams, but also in the development teams” Key notes : messages clés (3/7) Behavior Features Learning “Automation is the most critical piece of this whole puzzle”
- 13. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Key notes : messages clés (4/7) Behavior Features Learning 210 services et fonctionnalités de sécurité “We have over 100,000 subscriptions for security products in AWS Marketplace, (…) 10% of all of the subscriptions are in the security category, which I think is really cool. It's a testament to the fact that the process works.”
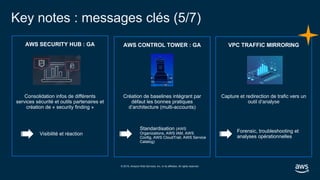
- 14. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Key notes : messages clés (5/7) AWS SECURITY HUB : GA Consolidation infos de différents services sécurité et outils partenaires et création de « security finding » AWS CONTROL TOWER : GA Création de baselines intégrant par défaut les bonnes pratiques d’architecture (multi-accounts) VPC TRAFFIC MIRRORING Capture et redirection de trafic vers un outil d’analyse Visibilité et réaction Standardisation (AWS Organizations, AWS IAM, AWS Config, AWS CloudTrail, AWS Service Catalog) Forensic, troubleshooting et analyses opérationnelles
- 15. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Key notes : messages clés (6/7) AWS MARKETPLACE PROCUREMENT : system integration Intégration avec les systèmes d’achat (Coupa, cXML) : contrôle de coûts, centralisation des achats CHIFFREMENT : « encrypt everything » Chiffrement des nouveaux EBS par défaut (+ backbones, entre bâtiments, machines, …) AWS CERTIFICATE MANAGER : hiérarchies racines Création d’une hiérarchie privée, avec autorités de certification racine et subordonnées Réduction des barrières à l’entrée pour tester et acquérir de nouveaux outils Sécurité « by default » et cohérence (défense en profondeur) Hiérarchie complète sans gérer des autorités de certification racines externes
- 16. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. “How to maintain security at scale as we continue to grow so rapidly…?” Key notes : messages clés (7/7) “With only three years in the market, we see trillions of executions every single month and have hundreds of thousands of active customers every month using AWS Lambda” (...) « Empowering devops people » Automated reasoning / provable security (Zelkova / Tiros) https://www.allthingsdistributed.com/2019/06/proving- security-at-scale-with-automated- reasoning.html?utm_campaign=website&utm_source=Last %20Week%20in%20AWS&utm_medium=email
- 17. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Agenda 1. Introduction au re:Inforce 2. Keynote : messages clés 3. Focus sur quelques annonces 4. Conclusion
- 18. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Traffic Mirroring
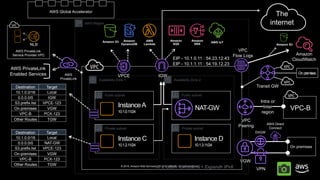
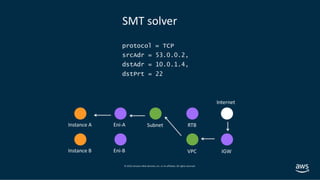
- 19. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. NAT Instance B 10.1.1.11/24 Instance BNAT-GW NAT-GW 0.0.0.0/0 AWS Region Availability Zone 2Availability Zone 1 Private subnet VGW VPC Peering VPC Flow Logs VPN The internet Private subnet Public subnet InstanceA Public subnet Amazon S3 VPC CIDR 10.1.0.0/16 10.1.0.11/24 Instance C 10.1.2.11/24 Instance D 10.1.3.11/24 DXGW + Expand+ IPv6 IGWVPCE 10.1.0.0/16 Local 0.0.0.0/0 IGW S3.prefix.list VPCE-123 On-premises VGW VPC-B PCX-123 Destination Target Intra or Inter region 10.1.0.0/16 Local S3.prefix.list VPCE-123 On-premises VGW VPC-B PCX-123 Destination Target AWS PrivateLink Service Provider VPC NLB On premises VPC-B EIP - 10.1.0.11 : 54.23.12.43 EIP - 10.1.1.11 : 54.19.12.23 Amazon DynamoDB AWS Lambda AWS Direct Connect Amazon SQS Amazon SNS AWS IoT Amazon CloudWatch AWS PrivateLink Transit GW On premises AWS PrivateLink Enabled Services Other Routes TGW Other Routes TGW Amazon S3 AWS Global Accelerator
- 20. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Amazon VPC Flow Logs
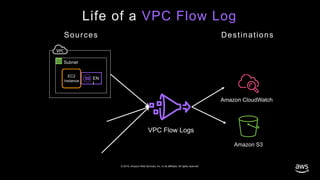
- 21. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Life of a VPC Flow Log Subnet
- 22. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. What did that flow log look like?
- 23. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Amazon VPC Traffic Mirroring
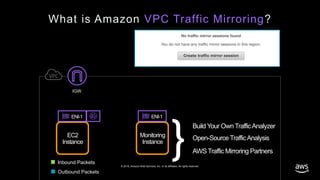
- 24. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. What is Amazon VPC Traffic Mirroring? EC2 Instance Inbound Packets Outbound Packets Monitoring Instance ENI-1 ENI-1 }Open-Source TrafficAnalysis Build Your Own TrafficAnalyzer AWS Traffic Mirroring Partners IGW
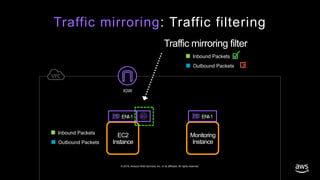
- 25. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. EC2 Instance Inbound Packets Outbound Packets Monitoring Instance ENI-1 ENI-1 Traffic mirroring filter Inbound Packets Outbound Packets X IGW Traffic mirroring: Traffic filtering
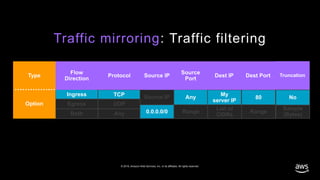
- 26. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Traffic mirroring: Traffic filtering Ingress TCP Single Source IP Single Range List of CIDRs Range Egress Both UDP Any Source IP Y/N Sample (Bytes) List of CIDRs
- 27. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Traffic mirroring: Traffic filtering Ingress TCP List of CIDRs Single Source IP SingleIngress TCP Any My server IP 80 Range List of CIDRs Range Egress Both UDP Any Source IP Y/N Sample (Bytes) No 0.0.0.0/0
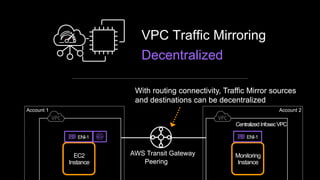
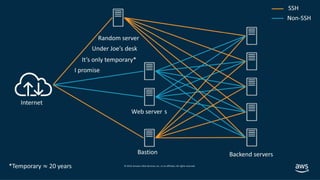
- 28. Decentralized Monitoring Instance ENI-1 ENI-1 EC2 Instance With routing connectivity, Traffic Mirror sources and destinations can be decentralized CentralizedInfosecVPC VPC Peering AWS Transit Gateway Account 1 Account 2
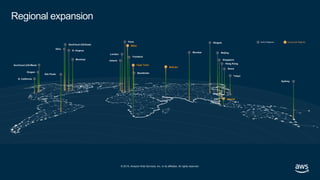
- 30. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Regional expansion Stockholm Bahrain Cape Town Hong Kong Milan Jakarta Announced Regions
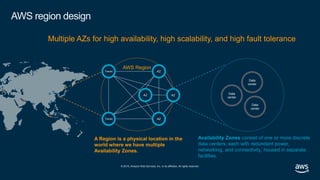
- 31. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. AWS region design Multiple AZs for high availability, high scalability, and high fault tolerance AWS Region AZ AZ AZ AZ Transit Transit Data center Data center Data center A Region is a physical location in the world where we have multiple Availability Zones. Availability Zones consist of one or more discrete data centers, each with redundant power, networking, and connectivity, housed in separate facilities.
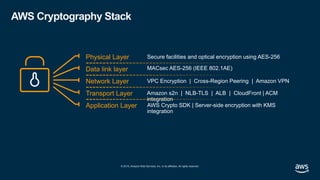
- 32. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. AWS Cryptography Stack Physical Layer Secure facilities and optical encryption using AES-256 VPC Encryption | Cross-Region Peering | Amazon VPN Amazon s2n | NLB-TLS | ALB | CloudFront | ACM integration AWS Crypto SDK | Server-side encryption with KMS integration Data link layer Network Layer Transport Layer Application Layer MACsec AES-256 (IEEE 802.1AE)
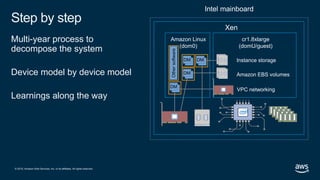
- 33. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Intel mainboard Step by step Multi-year process to decompose the system Device model by device model Learnings along the way Amazon EBS volumes DM Instance storage VPC networking DM Othersoftware DM DM Amazon Linux (dom0) cr1.8xlarge (domU/guest) Xen
- 34. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. • Missionary, passionate, and uniquely talented team • Shared our vision for hardware innovation and the cloud • Deep experience in both networking and storage
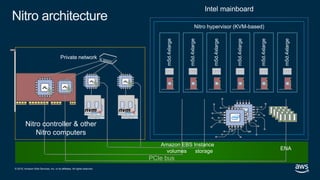
- 35. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. PCIe bus Amazon RDS Nitro hypervisor (KVM-based) Instance storage Intel mainboard Nitro architecture ENA Private network m5d.4xlarge m5d.4xlarge m5d.4xlarge m5d.4xlarge m5d.4xlarge m5d.4xlarge Nitro controller & other Nitro computers Amazon EBS volumes
- 36. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Encryption—performance Hardware acceleration allows for line-rate AES-256 encryption No Dom0 in Nitro hypervisor—greater simplicity and safety No SSH or other interactive modes anywhere—no direct human access Hypervisor awaits commands from Nitro controller Nitro controller awaits commands from the external control plane Outbound communications from either layer are a clear sign of compromise and are treated accordingly
- 37. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Post-Quantum
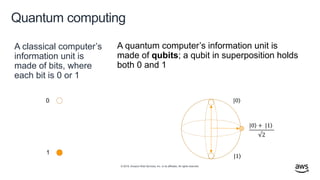
- 38. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Quantum computing A classical computer’s information unit is made of bits, where each bit is 0 or 1 0 1 A quantum computer’s information unit is made of qubits; a qubit in superposition holds both 0 and 1 ۧ|0 ۧ|0 + ۧ|1 √2 ۧ|1
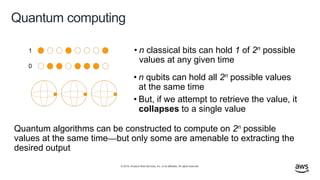
- 39. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Quantum computing 1 0 • n classical bits can hold 1 of 2n possible values at any given time • n qubits can hold all 2n possible values at the same time • But, if we attempt to retrieve the value, it collapses to a single value Quantum algorithms can be constructed to compute on 2n possible values at the same time—but only some are amenable to extracting the desired output
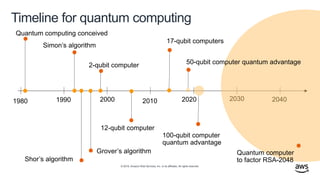
- 40. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Impact of quantum computing on cryptography Shor’s algorithm (1994): Can solve the discrete log problem (breaking Diffie–Hellman and elliptic curve cryptography) and factor composite numbers (breaking RSA) Grover’s algorithm (1996): Can search an unsorted database of N items in Ο( 𝑁 ) time (reducing the security of symmetric ciphers and pre-image search for hash functions)
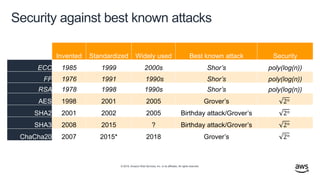
- 41. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Security against best known attacks Invented Standardized Widely used Best known attack Security ECC 1985 1999 2000s Shor’s poly(log(n)) FF 1976 1991 1990s Shor’s poly(log(n)) RSA 1978 1998 1990s Shor’s poly(log(n)) AES 1998 2001 2005 Grover’s 2 𝑛 SHA2 2001 2002 2005 Birthday attack/Grover’s 2 𝑛 SHA3 2008 2015 ? Birthday attack/Grover’s 2 𝑛 ChaCha20 2007 2015* 2018 Grover’s 2 𝑛
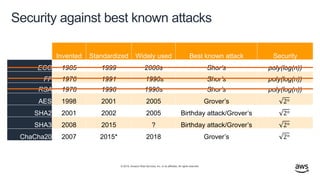
- 42. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Security against best known attacks Invented Standardized Widely used Best known attack Security ECC 1985 1999 2000s Shor’s poly(log(n)) FF 1976 1991 1990s Shor’s poly(log(n)) RSA 1978 1998 1990s Shor’s poly(log(n)) AES 1998 2001 2005 Grover’s 2 𝑛 SHA2 2001 2002 2005 Birthday attack/Grover’s 2 𝑛 SHA3 2008 2015 ? Birthday attack/Grover’s 2 𝑛 ChaCha20 2007 2015* 2018 Grover’s 2 𝑛
- 43. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Timeline for quantum computing
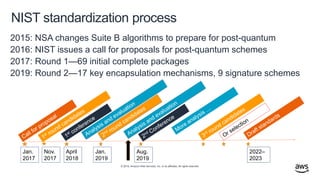
- 44. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. NIST standardization process 2015: NSA changes Suite B algorithms to prepare for post-quantum 2016: NIST issues a call for proposals for post-quantum schemes 2017: Round 1—69 initial complete packages 2019: Round 2—17 key encapsulation mechanisms, 9 signature schemes Jan. 2017 Nov. 2017 April 2018 Aug. 2019 2022– 2023 Jan. 2019
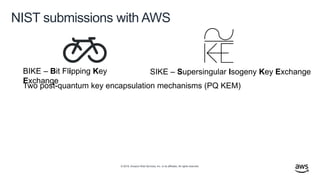
- 45. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. NIST submissions with AWS BIKE – Bit Flipping Key Exchange SIKE – Supersingular Isogeny Key Exchange Two post-quantum key encapsulation mechanisms (PQ KEM)
- 46. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Provable Security Deep Dive S E P 2 0 1 + G R C 3 0 1
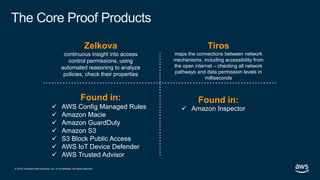
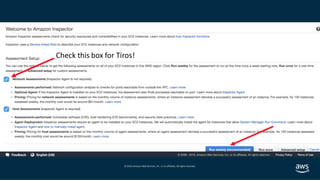
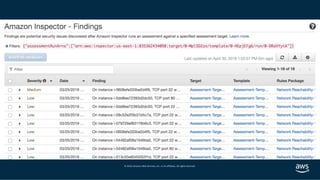
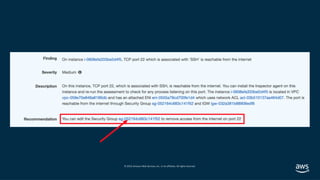
- 48. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Zelkova continuous insight into access control permissions, using automated reasoning to analyze policies, check their properties The Core Proof Products Tiros maps the connections between network mechanisms, including accessibility from the open internet – checking all network pathways and data permission levels in milliseconds Found in: AWS Config Managed Rules Amazon Macie Amazon GuardDuty Amazon S3 S3 Block Public Access AWS IoT Device Defender AWS Trusted Advisor Found in: Amazon Inspector
- 56. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Agenda 1. Introduction au re:Inforce 2. Keynote : messages clés 3. Focus sur quelques annonces 4. Conclusion
- 57. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Conclusion
- 58. © 2019, Amazon Web Services, Inc. or its affiliates. All rights reserved. Merci !