Business Dimension of Expanded Password System
- 1. Introduction for business people of Expanded Password System Security of the real/cyber-fused society hinges on “Assured Identity”, which hinges on “Shared Secrets” in cyberspace. The text password has been the shared secrets for many decades. We now need a successor to the text password. There exists a promising candidate, an Expanded Password System (EPS) which accepts images as well as characters and which generates a high-entropy password from a hard-to-forget images and texts. 20th April, 2015 Mnemonic Security, Inc., Japan/UK
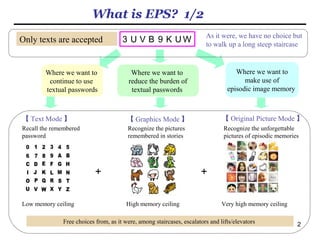
- 2. 2 What is EPS? 1/3 Only texts are accepted As it were, we have no choice but to walk up a long steep staircase Where we want to continue to use textual passwords Where we want to reduce the burden of textual passwords Where we want to make use of episodic image memory 3UVB9KUW 【 Text Mode 】 【 Graphics Mode 】 【 Original Picture Mode 】 Recall the remembered password Recognize the pictures remembered in stories Recognize the unforgettable pictures of episodic memories Free choices from, as it were, among staircases, escalators and lifts/elevators Low memory ceiling Very high memory ceilingHigh memory ceiling + +
- 3. There are several known pictures. I can easily find all of them right away. Only I can select all of them correctly. Practicable even in panic when images of episodic memory are registered Incorporating the function of generating high-entropy online passwords from hard-to-forget images and texts. Security of real/cyber-fused society hinges on online identity assurance Online identity assurance hinges on shared secrets, i.e. what we remember Video: http://www.youtube.com/watch?v=Q8kGNeIS2Lc What is EPS? 2/3 Technical details available at http://www.slideshare.net/HitoshiKokumai/expanded-password-system
- 4. 4 What is EPS? 3/3 When unique matrices of images are allocated to different accounts with the EPS, those unique matrices of images will be telling you what images you could pick up as your passwords. Being able to recall strong passwords is one thing. Being able to recall the relations between accounts and the corresponding passwords is another. EPS frees us from the burden of managing the relations between accounts and the corresponding passwords. Account A Account B Account C Account D Account E, F, G, H, I, J, K, L-----------
- 5. 5 What problems is EPS expected to solve? - White House cyber czar's goal: 'Kill the password dead' http://www.federalnewsradio.com/241/3646015/White-House-cyber-czars-goal-Kill-the-password-dead “He cited studies showing as much as 80 percent of cyber intrusions — "some ridiculously high number," he said — are caused by exploiting weak or stolen passwords.” - Cybercrime and espionage costs $445 billion annually http://www.washingtonpost.com/world/national-security/report-cybercrime-and-espionage-costs-445-billion-annually/2014/06/09/8995291c-ecce- 11e3-9f5c-9075d5508f0a_story.html “CSIS used several methods to arrive at a range of estimates, from $375 billion to as much as $575 billion.” - Passwords Still Pose Big Security Risks http://www.paymentssource.com/news/passwords-still-pose-big-security-risks-3018257-1.html “Many “advanced data stealing attacks” happen simply from poor password practices.” - Soon Hackers May Topple Global Economy http://i-hls.com/2014/05/report-soon-hackers-may-topple-global-economy/?utm_source=rss&utm_medium=rss&utm_campaign=report-soon- hackers-may-topple-global-economy&utm_source=Meital&utm_medium=Meital&utm_campaign=RSS “Within the next five to seven years, as much as $21 trillion in global economic-value creation depends on robust cyber security”.
- 6. 6 Why EPS? Biometric products operated in cyber space require the password called a backup/fallback password to be registered in case of false rejection (footnoted on the next page). Action patterns are too difficult to replay accurately and also require the fallback password in case of false rejection. Multi-factor authentications require the password as one of the factors.. ID federations (single-sign-on services and password management tools) are operated with the password called “master-password”. PIN and passphrases belong to the password. As such we are unable to live without the password and yet it is obvious that the conventional character password no longer suffices. Here enter the EPS, a password system expanded to accept images on top of characters, which is expected to play a very significant role.
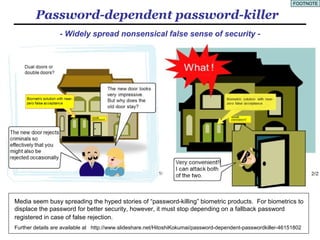
- 7. Password-dependent password-killer - Widely spread nonsensical false sense of security - Media seem busy spreading the hyped stories of “password-killing” biometric products. For biometrics to displace the password for better security, however, it must stop depending on a fallback password registered in case of false rejection. Further details are available at http://www.slideshare.net/HitoshiKokumai/password-dependent-passwordkiller-46151802 FOOTNOTE
- 8. 8 What are our competitions? Setting aside the hyped stories of “password-dependent password-killer” solutions that are causing nonsensical false sense of security, among the broader password family are 1. Pattern-on-grid: The drawbacks of this method are (1) complicated patterns could have a very high entropy but humans cannot remember multiple numbers of such complicated patterns and (2) simple patterns like alphabets are easy to remember but are fully known to criminals as well. 2. Simple pictorial password: Not all the pictures are good for passwords. Pictures or outstanding features on pictures that we manage to remember afresh are subject to the cognitive phenomenon called “interference of memory” if not as badly as meaningless random characters. So it is still easy-to-break if it is easy-to-remember and hard-to-remember if it is hard-to-break. 3. Facelock: Researchers at York University who specialize in cognitive psychology came up with a competitive approach by using friends’ faces as the hard-to-forget passwords, which is far less subject to “interference of memory” and therefore users can manage many of them at a time, though it is not sufficiently hard-to-break. We have now teamed up with them. Remark: It is possible to deploy all the above on the EPS platform as the variations.
- 9. 9 What can EPS achieve? EPS can be viewed as an enhanced successor to text-only password systems on its own. Furthermore EPS enables us to see truly powerful multi-factor authentications with a strong unique password being used as one of the factors for all different accounts, whether indoor or outdoor. With EPS used for fallback passwords in case of false rejection, biometric solutions will offer good convenience without much sacrificing the confidentiality. We would also be able to see truly reliable decentralized ID federations with a strong unique password being used as the master-password for each of single- sign-on services and password management tools. The outcome will be the most highly assured identity achieved through the most reliable “shared secrets”, which is indispensable for the coming age of Electronic Healthcare, Pandemic-resistant Teleworking, ICT-assisted Disaster Prevention, Rescue & Recovery, Hands-Free Operation of Wearable Computing, Hands-Free Payment & Empty-Handed Shopping, Humanoid Robots, Internet of Things and, needless to say, Cyber Defence & Law Enforcement along with the basic need of real/cyber-fused social life.
- 10. 10 What market potential does EPS have? With billions of people suffering the same big headache, the problem to be addressed by our solution is huge, Substantial revenues will be expected for the business of providing the most practicable solution. Global sales forecasts are difficult to figure out at this stage. The number of some US$1 million over the past non-turbulent 10 years that we experienced in Japan probably does not make a good clue to the figures for the globally turbulent future. The vacuum for comprehensive and practicable solutions will probably be just vast that will come up in front of us when the hyped misleading stories of "password-killer" solutions have evaporated. The sales in 3 - 5 years' time could be in the order of $10m or $100m or $1bn. How quickly we can reach $100m sales will largely hinge on how quickly the false sense of security about the "password-dependent password-killer" biometric products gets killed dead. For people who take it for granted that the password problem will eventually be solved by the dazzling “password-killer” solutions would find it difficult to agree with us that our products will have a sizeable share on the market for the solutions to the password problem.
- 11. 11 What EPS products are available? a. Server software for online-access b. Server software for onetime password generation c. Server software for single sign on with OpenID protocol d. Client software for Windows PC logon e. Client software for smart devices logon f. Client software for “image”-to-”text password” conversion g. Library for general purpose h. Client CryptoMnemo software with data encryption function i. Client Authority-distributed CryptoMnemo for prevention of insiders’ crime j. Server-Client extension for (i). * Some four million dollars, half of which from the Japanese government, have been invested into the research and development of the above product lineup. ** All the above products were developed in Japanese for Japanese customers. With the algorithm fully completed, all of them can be put on the global market straight away when re- written in English.
- 12. 12 What sectors should be first taken up? Among such new frontiers as Electronic Healthcare, Pandemic-resistant Teleworking, ICT-assisted Disaster Prevention, Rescue & Recovery, Hands-Free Operation of Wearable Computing, Hands-Free Payment & Empty-Handed Shopping, Humanoid Robots, Internet of Things, Cyber Defence & Law Enforcement along with the basic need of real/cyber-fused social life, the sectors that should be looked at first are 1. Where secure identity assurance is needed for elderly people for whom character passwords are too difficult. 2. Where people have to get their identity proven securely even when they are caught in panic 3. Where people have to safely manage many numbers of accounts each of which requires a unique strong password.
- 13. 13 Who are we? Hitoshi Kokumai, Inventor of Mnemonic Guard, pioneer of Expanded Password System, and Founder of Mnemonic Security, Inc. He used to work for a UK company whose original name was Nairn International Limited, a part of Unilever in 1984, as a contract business development coordinator. Over the 22 years of service until 2006 he contributed to UK’s export of some 100 million Pounds through 60 trips between UK and Japan. He was graduated from Economics Faculty of Kyoto University in 1971. Ryuhei Masuno, Co-Founder of Mnemonic Security, Inc. Before joining Hitoshi Kokumai for this business, he used to be a member of the board of Asahipen, a paints and home products manufacturer listed at Osaka Stock Exchange where he was responsible for accounting and general corporate management. He was graduated from the Law Faculty of Kyoto University in 1972.
- 14. 14 In Conclusion We are in the middle of the decades-long game of having the finalist candidates chosen for the legitimate successors not just to the decades-old character passwords but to the centuries or millennia-old seals and signatures, which will make the basic foundation for the real/cyber-fused society that may well last for more than generations or even centuries for the whole global population. Please join us and support us for this nice exciting enterprise. For any further information, please feel free to contact Hitoshi Kokumai at Mail: kokumai@mneme.co.jp Skype: kokumaiskype Tel: 81 – 90 – 5460 – 7350 (when staying in Japan) 44 – 7738 – 905032 (when staying in UK)